Security
Elevate your cloud security strategy with  robust suite of features tailored to fortify your digital defenses. With Cloud Security Posture Management (CSPM) Dashboards, gain real-time insights into your security posture, identifying misconfigurations and vulnerabilities across your cloud infrastructure. Seamlessly integrate with Security Information and Event Management (SIEM) Dashboards to monitor and analyze security events in real-time, ensuring rapid threat detection and response. Take control with Infrastructure as Code (IaC) Dashboards, allowing you to enforce security policies from the get-go, ensuring your cloud deployments are secure from the ground up. CloudCatcher isn’t just a solution; it’s your shield against cyber threats.
robust suite of features tailored to fortify your digital defenses. With Cloud Security Posture Management (CSPM) Dashboards, gain real-time insights into your security posture, identifying misconfigurations and vulnerabilities across your cloud infrastructure. Seamlessly integrate with Security Information and Event Management (SIEM) Dashboards to monitor and analyze security events in real-time, ensuring rapid threat detection and response. Take control with Infrastructure as Code (IaC) Dashboards, allowing you to enforce security policies from the get-go, ensuring your cloud deployments are secure from the ground up. CloudCatcher isn’t just a solution; it’s your shield against cyber threats.
 robust suite of features tailored to fortify your digital defenses. With Cloud Security Posture Management (CSPM) Dashboards, gain real-time insights into your security posture, identifying misconfigurations and vulnerabilities across your cloud infrastructure. Seamlessly integrate with Security Information and Event Management (SIEM) Dashboards to monitor and analyze security events in real-time, ensuring rapid threat detection and response. Take control with Infrastructure as Code (IaC) Dashboards, allowing you to enforce security policies from the get-go, ensuring your cloud deployments are secure from the ground up. CloudCatcher isn’t just a solution; it’s your shield against cyber threats.
robust suite of features tailored to fortify your digital defenses. With Cloud Security Posture Management (CSPM) Dashboards, gain real-time insights into your security posture, identifying misconfigurations and vulnerabilities across your cloud infrastructure. Seamlessly integrate with Security Information and Event Management (SIEM) Dashboards to monitor and analyze security events in real-time, ensuring rapid threat detection and response. Take control with Infrastructure as Code (IaC) Dashboards, allowing you to enforce security policies from the get-go, ensuring your cloud deployments are secure from the ground up. CloudCatcher isn’t just a solution; it’s your shield against cyber threats. 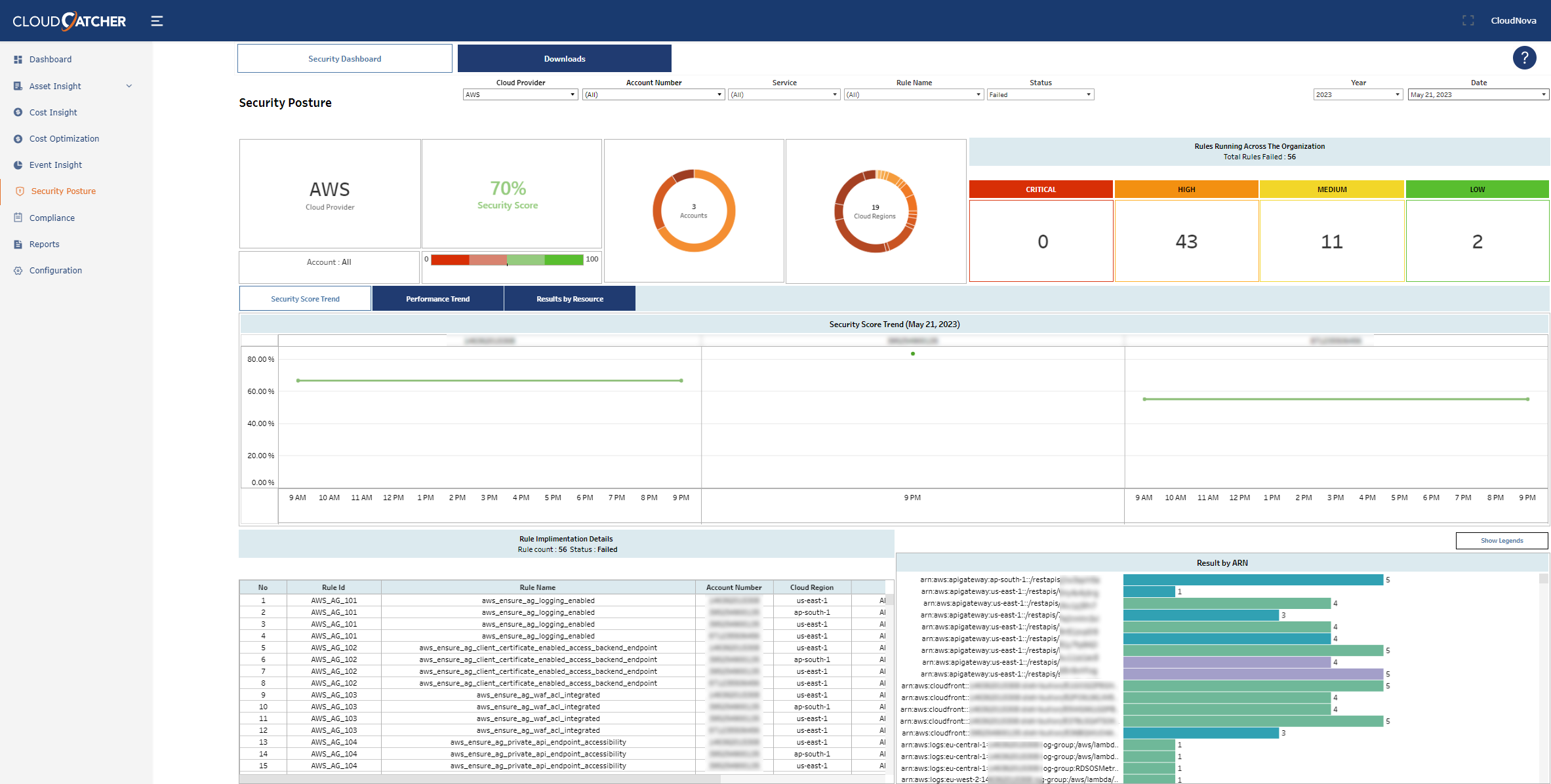
CSPM
 provides the ability to achieve a strong security posture by validating your cloud asset posture against the best practices from the Center for Internet Security (CIS). CloudCatcher maps the CIS controls to a broad number of industry security benchmarks, with hundreds of pre-built policies. We support multiple security standards, including ones developed by CloudNova technologies, LLC.
CloudCatcher Cloud Security Posture Management (CSPM) module provides comprehensive metrics on security posture of the cloud environment by scanning configuration settings of all cloud resources. As an example, CloudCatcher identifies lack of encryption on databases or data storage, lack of encryption on application traffic, improper encryption key management such as not rotating keys regularly, lack of multi-factor authentication on critical system accounts, misconfigured network connectivity, overly permissive access rules or resources directly accessible from the internet, data storage exposed directly to the internet, logging is not turned on to monitor critical activities such as network flows, database access, or privileged user activity.
provides the ability to achieve a strong security posture by validating your cloud asset posture against the best practices from the Center for Internet Security (CIS). CloudCatcher maps the CIS controls to a broad number of industry security benchmarks, with hundreds of pre-built policies. We support multiple security standards, including ones developed by CloudNova technologies, LLC.
CloudCatcher Cloud Security Posture Management (CSPM) module provides comprehensive metrics on security posture of the cloud environment by scanning configuration settings of all cloud resources. As an example, CloudCatcher identifies lack of encryption on databases or data storage, lack of encryption on application traffic, improper encryption key management such as not rotating keys regularly, lack of multi-factor authentication on critical system accounts, misconfigured network connectivity, overly permissive access rules or resources directly accessible from the internet, data storage exposed directly to the internet, logging is not turned on to monitor critical activities such as network flows, database access, or privileged user activity. CSPM

 provides the ability to achieve a strong security posture by validating your cloud asset posture against the best practices from the Center for Internet Security (CIS). CloudCatcher maps the CIS controls to a broad number of industry security benchmarks, with hundreds of pre-built policies. We support multiple security standards, including ones developed by CloudNova technologies, LLC.
CloudCatcher Cloud Security Posture Management (CSPM) module provides comprehensive metrics on security posture of the cloud environment by scanning configuration settings of all cloud resources. As an example, CloudCatcher identifies lack of encryption on databases or data storage, lack of encryption on application traffic, improper encryption key management such as not rotating keys regularly, lack of multi-factor authentication on critical system accounts, misconfigured network connectivity, overly permissive access rules or resources directly accessible from the internet, data storage exposed directly to the internet, logging is not turned on to monitor critical activities such as network flows, database access, or privileged user activity.
provides the ability to achieve a strong security posture by validating your cloud asset posture against the best practices from the Center for Internet Security (CIS). CloudCatcher maps the CIS controls to a broad number of industry security benchmarks, with hundreds of pre-built policies. We support multiple security standards, including ones developed by CloudNova technologies, LLC.
CloudCatcher Cloud Security Posture Management (CSPM) module provides comprehensive metrics on security posture of the cloud environment by scanning configuration settings of all cloud resources. As an example, CloudCatcher identifies lack of encryption on databases or data storage, lack of encryption on application traffic, improper encryption key management such as not rotating keys regularly, lack of multi-factor authentication on critical system accounts, misconfigured network connectivity, overly permissive access rules or resources directly accessible from the internet, data storage exposed directly to the internet, logging is not turned on to monitor critical activities such as network flows, database access, or privileged user activity. SIEM
 Security information and event management (SIEM) aggregate relevant data from multiple sources, identify deviations from the norm and highlight actionable items to take appropriate remediation actions. CloudCatcher employs rule-based statistical correlation engine to make connections between event log entries with ML to include user and entity behavior analytics, as well as security orchestration, automation, and response.
Security information and event management (SIEM) aggregate relevant data from multiple sources, identify deviations from the norm and highlight actionable items to take appropriate remediation actions. CloudCatcher employs rule-based statistical correlation engine to make connections between event log entries with ML to include user and entity behavior analytics, as well as security orchestration, automation, and response. 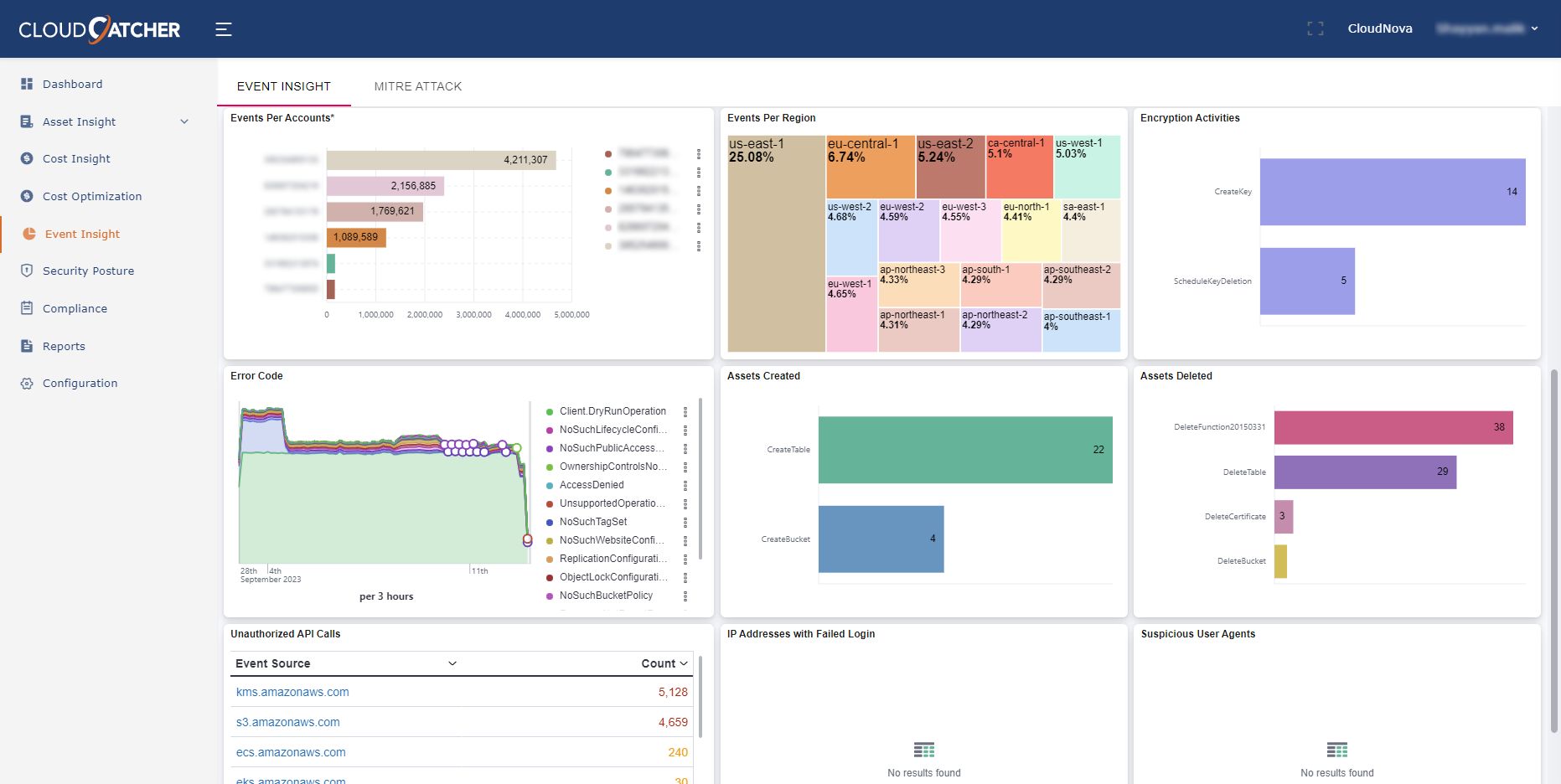
SIEM

 Security information and event management (SIEM) aggregate relevant data from multiple sources, identify deviations from the norm and highlight actionable items to take appropriate remediation actions. CloudCatcher employs rule-based statistical correlation engine to make connections between event log entries with ML to include user and entity behavior analytics, as well as security orchestration, automation, and response.
Security information and event management (SIEM) aggregate relevant data from multiple sources, identify deviations from the norm and highlight actionable items to take appropriate remediation actions. CloudCatcher employs rule-based statistical correlation engine to make connections between event log entries with ML to include user and entity behavior analytics, as well as security orchestration, automation, and response. IaC Scanning
 Infrastructure as a Code (IaC) Scanning module scans IaC configuration files for known vulnerabilities.Our IaC Scanning supports a wide range of platforms including Terraform, AWS CloudFormation, Kubernetes, Docker, Ansible, and Helm, ensuring your infrastructure remains secure and compliant across these popular solutions.”
Infrastructure as a Code (IaC) Scanning module scans IaC configuration files for known vulnerabilities.Our IaC Scanning supports a wide range of platforms including Terraform, AWS CloudFormation, Kubernetes, Docker, Ansible, and Helm, ensuring your infrastructure remains secure and compliant across these popular solutions.”




















IaC Scanning
 Infrastructure as a Code (IaC) Scanning module scans IaaC configuration files for known vulnerabilities. Our IaaC Scanning supports a wide range of platforms including Terraform, AWS CloudFormation, Kubernetes, Docker, Ansible, and Helm, ensuring your infrastructure remains secure and compliant across these popular solutions.”
Infrastructure as a Code (IaC) Scanning module scans IaaC configuration files for known vulnerabilities. Our IaaC Scanning supports a wide range of platforms including Terraform, AWS CloudFormation, Kubernetes, Docker, Ansible, and Helm, ensuring your infrastructure remains secure and compliant across these popular solutions.”